
IEC-62443 is a series of standards including technical reports to secure Industrial Automation and Control Systems (IACS). It provides a systematic and practical approach to cybersecurity for industrial systems. Every stage and aspect of industrial cybersecurity is covered, from risk assessment through operations.
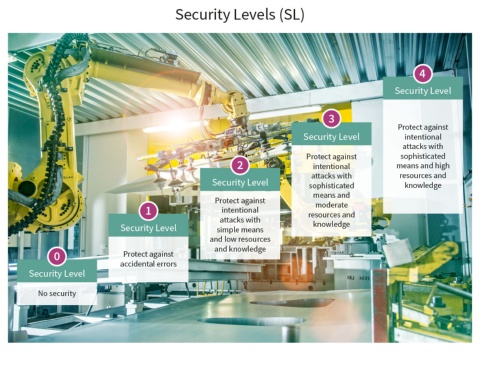
Using the techniques described in IEC 62443, industrial stakeholders can assess the cybersecurity risks to each system and decide how to address those risks. Recognizing that not every system is equally critical, IEC 62443 defines five security levels (SLs): from SL 0 (no security) to SL 4 (resistant against nation-state attacks).
Specific security requirements are defined for each security level so each industrial system will have the right security, protecting uptime, safety, and intellectual property. All parties in the industrial ecosystem benefit from having clear expectations: asset owners and operators, systems integrators, equipment and service providers, and regulators.
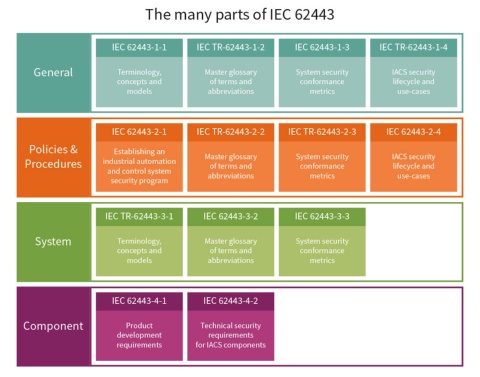
IEC 62443 is organized into the following four categories: General, Policies and Procedures, System, and Component:
- The General documents provide an overview of the industrial security process and introduce essential concepts.
- The documents on Policies & Procedures highlight the importance of policies - even the best security is useless if people are not trained and committed to supporting it.
- Because security can only be understood as an integrated system, the System documents provide essential guidance on designing and implementing secure systems.
- And because one cannot build a solid building out of weak bricks, the Component documents describe the requirements that must be met for secured industrial components.
IEC 62443 requires hardware security for Security Levels 3 and 4. Why hardware?
- Discrete hardware security chips are much more secure than pure software security. Software can easily be analyzed by attackers to find vulnerabilities and develop exploits that undermine security. Such attacks appear every day. Tamper-resistant hardware security chips efficiently prevent such attacks.
- Most hardware security chips are evaluated and certified by independent security testing laboratories. These certifications prove highest barriers to penetrate the chip's defenses. Anybody can claim to provide security - but for critical applications, independent expert evaluation is required.
- Hardware security reduces engineering and support costs. Custom-built security is expensive to build and requires constant maintenance. Choosing an Infineon security chip instead leverages our decades of security expertise.
For these reasons and others, security experts agree that tamper-resistant security hardware is the best approach for critical systems. That's why IEC 62443 requires it.

